Commoninfo:stealthaddress: Difference between revisions
| [checked revision] | [checked revision] |
No edit summary |
CryptoUser (talk | contribs) No edit summary |
||
| Line 1: | Line 1: | ||
{{#seo: | {{#seo: | ||
|title= | |title= Stealth address — Decimal Wiki | ||
|titlemode= append | |titlemode= append | ||
|keywords= Stealth address | |keywords= Stealth address, Hidden address | ||
|description= | |description= Hidden (stealth) address | ||
}} | }} | ||
'''Stealth address''' is a privacy enhancement technology that protects the privacy of [[cryptocurrency]] recipients. | |||
Standard [[transaction]]s in the [[blockchain]] are "pseudo-anonymous", since all the details of transfers are visible in the public register. Transaction details are identified only by their [[blockchain address|blockchain addresses]]. This means that a "certain" address is associated with one person, who, in turn, is not unknown to the public. | |||
'''However, there is a possibility of complete depersonalization of [[wallet]] owners.''' | |||
[[ | == History == | ||
The simplest stealth address scheme was first developed in 2011; it relied on the [[ECDH|Diffie-Hellman Elliptic Curve Protocol (ECDH)]]. To eliminate the design flaws of the first hidden addresses, the improved scheme was described in detail by [[wikipedia:Nicholas van Saberhagen|Nicholas van Saberhagen]] in 2013, and was later adapted by [[wikipedia:Peter Todd|Peter Todd]] in the [[Bitcoin]] protocol in 2014. | |||
''' | '''The stealth address mechanism uses a combination of different [[public key|public]] and [[private key|private keys]], which are dynamic and intended for one-time use only.''' | ||
== Varieties of stealth address protocols == | |||
* Basic Stealth Address Protocol ([[BSAP]]). | |||
* Improved Stealth Address Protocol ([[ISAP]]). | |||
* Stealth Address Dual Key Protocol ([[DKSAP]]). | |||
== Operation principle == | |||
[[File:Commoninfo-image_2021-05-07_16_11_58.jpg|500px|thumb|right]] | |||
''Stealth addresses require a random and one-time address from the sender for each transaction on behalf of the recipient, so that different payments made to the same recipient are not related.'' | |||
'''Example:''' | |||
''' | |||
Alice holds five coins on a blockchain with the support of a hidden address. Alice has full control over her [[token]]s as long as they are on her [[electronic wallet]]. If she wants to send [[coin]]s to Bob, Bob will generate a [[transaction]] output that will tell the [[network]] that Alice is sending Bob five tokens. Now Bob becomes the rightful owner of five tokens. | |||
Alice's wallet will use Bob's [[public address]] by combining it with random data strings that are generated to output tokens to Bob's address. While other network users can see the transaction record, no one except Alice and Bob will know that the transaction took place between Alice and Bob. | |||
Using the private key of viewing his own wallet, Bob will be able to find a transaction on the blockchain and receive [[coin]]s. Using a one-time private key corresponding to the one-time public key for the transaction, Bob will get the right to spend cryptocurrency. '''The addresses of the sender's or recipient's wallets are not published anywhere in this process.''' | |||
''Since these randomly generated one-time addresses are created for each transaction on behalf of the recipient, stealth addresses add an additional layer of privacy in the world of cryptocurrencies.'' | |||
[[Category:Commoninfo]] | |||
[[Category:Crypto security]] | |||
Latest revision as of 08:53, 15 February 2024
Stealth address is a privacy enhancement technology that protects the privacy of cryptocurrency recipients.
Standard transactions in the blockchain are "pseudo-anonymous", since all the details of transfers are visible in the public register. Transaction details are identified only by their blockchain addresses. This means that a "certain" address is associated with one person, who, in turn, is not unknown to the public.
However, there is a possibility of complete depersonalization of wallet owners.
History
The simplest stealth address scheme was first developed in 2011; it relied on the Diffie-Hellman Elliptic Curve Protocol (ECDH). To eliminate the design flaws of the first hidden addresses, the improved scheme was described in detail by Nicholas van Saberhagen in 2013, and was later adapted by Peter Todd in the Bitcoin protocol in 2014.
The stealth address mechanism uses a combination of different public and private keys, which are dynamic and intended for one-time use only.
Varieties of stealth address protocols
- Basic Stealth Address Protocol (BSAP).
- Improved Stealth Address Protocol (ISAP).
- Stealth Address Dual Key Protocol (DKSAP).
Operation principle
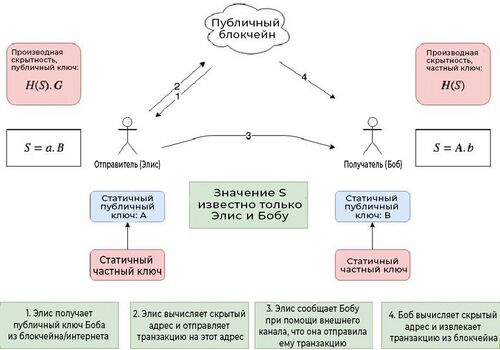
Stealth addresses require a random and one-time address from the sender for each transaction on behalf of the recipient, so that different payments made to the same recipient are not related.
Example:
Alice holds five coins on a blockchain with the support of a hidden address. Alice has full control over her tokens as long as they are on her electronic wallet. If she wants to send coins to Bob, Bob will generate a transaction output that will tell the network that Alice is sending Bob five tokens. Now Bob becomes the rightful owner of five tokens.
Alice's wallet will use Bob's public address by combining it with random data strings that are generated to output tokens to Bob's address. While other network users can see the transaction record, no one except Alice and Bob will know that the transaction took place between Alice and Bob.
Using the private key of viewing his own wallet, Bob will be able to find a transaction on the blockchain and receive coins. Using a one-time private key corresponding to the one-time public key for the transaction, Bob will get the right to spend cryptocurrency. The addresses of the sender's or recipient's wallets are not published anywhere in this process.
Since these randomly generated one-time addresses are created for each transaction on behalf of the recipient, stealth addresses add an additional layer of privacy in the world of cryptocurrencies.